Jamf Pro
Jump to navigation
Jump to search
Contents
JAMF Pro
Jamf Pro is JAMF's MDM solution – managing computers and devices
Single Sign On for JAMF Pro protects the JAMF Pro web app by redirecting Admin users to their IDP to authenticate and then directed back to the JAMF Pro Admin portal.
Single Sign On with Cloudwork
- Login to Cloudwork dashboard
- Navigate to Single Sign On>Add New Service>Custom SAML Service
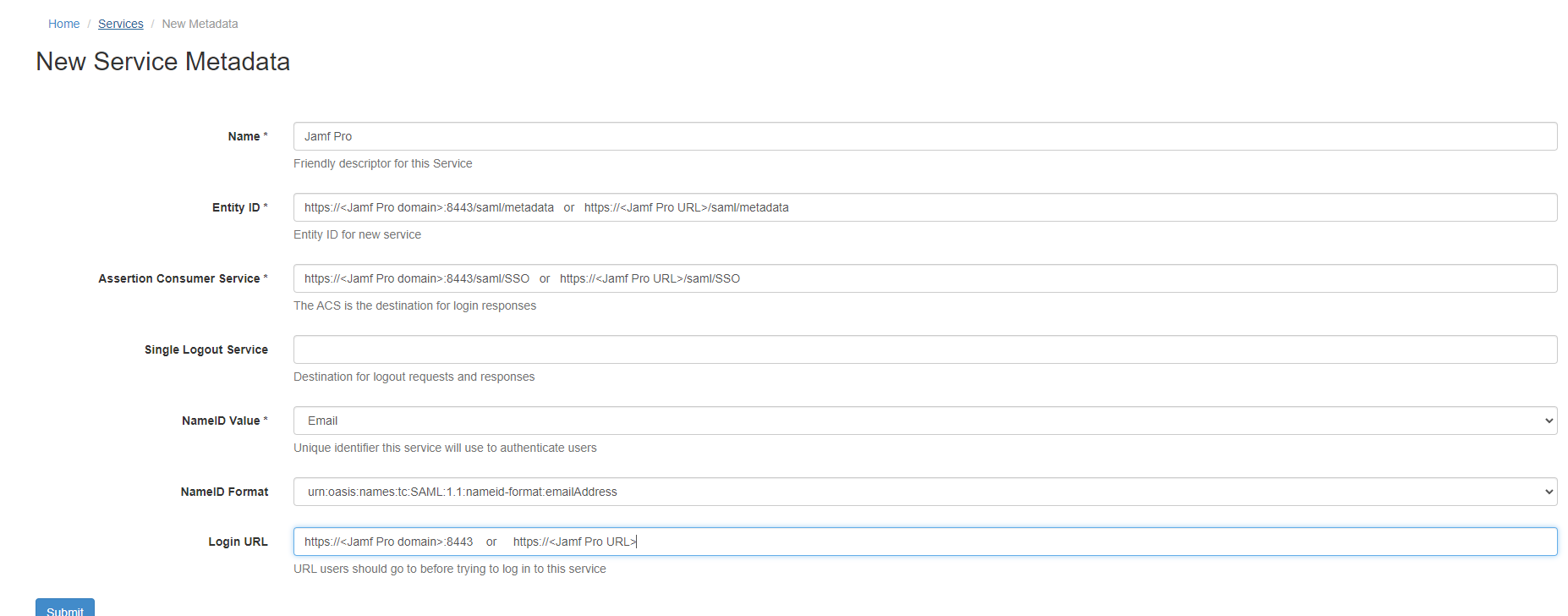
- Fill out the form:
- Name = JAMFPro
- Entity ID:
- If using JAMF OnPremise, use for Entity ID: https://<JAMF Pro domain>:8443/saml/metadata
- If using Jamfcloud hosted server, use for Entity ID: https://<JAMF Pro URL>/saml/metadata
- ACS:
- If using JAMF OnPremise, use for ACS: https://<JAMF Pro domain>:8443/saml/SSO
- If using Jamfcloud hosted server, use for ACS: https://<JAMF Pro URL>/saml/SSO
- Single Logout Service = Leave blank
- NameID Value = From the drop down select Email
- NameID Format = select from drop down urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
- Login URL:
- If using JAMF OnPremise, use for Login URL: https://<JAMF Pro domain>:8443
- If using Jamfcloud hosted server, use for Login URL: https://<JAMF Pro URL>
- Click Submit
- Under XML File click download and save file as .XML file
Single Sign On with JAMF Pro
- Login to your JAMF Pro dashboard
- In the top right corner click the gear
- Under System Settings click on Single Sign On
- In the bottom left corner click Edit and turn on Single Sign-On Authentication
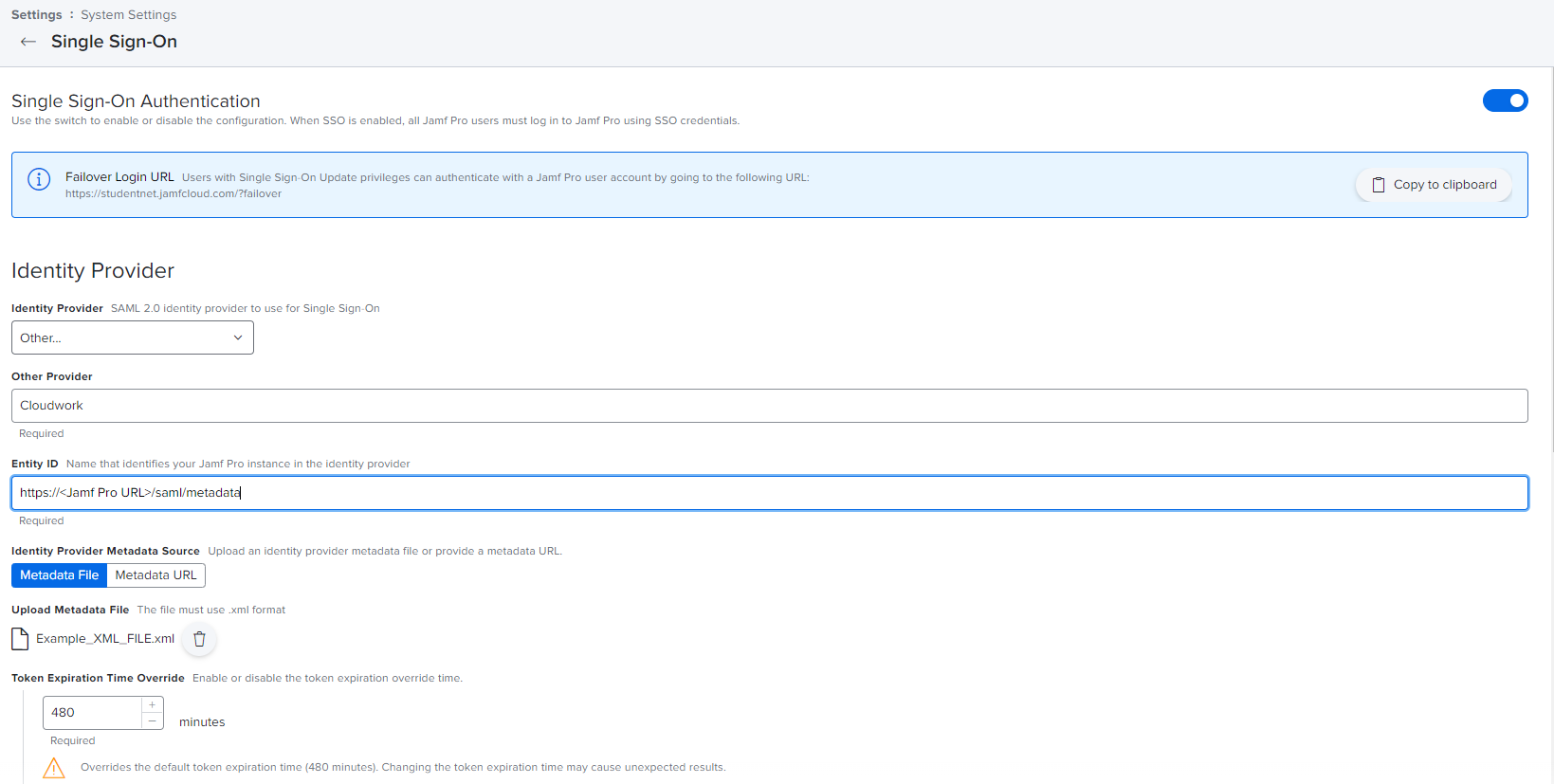
- Fill out the form:
- Identity Provider = Other
- Other Provider = Enter in Cloudwork
- Entity ID:
- If using JAMF OnPremise, use for Entity ID: https://<JAMF Pro domain>:8443/saml/metadata
- If using Jamfcloud hosted server, use for Entity ID: https://<JAMF Pro URL>/saml/metadata
- Identity Provider Metadata Source = select Metadata File
- Upload Metadata File = Upload the XML File which was downloaded from Cloudwork Dashboard.
- Token Expiration Time Override = Leave at 480
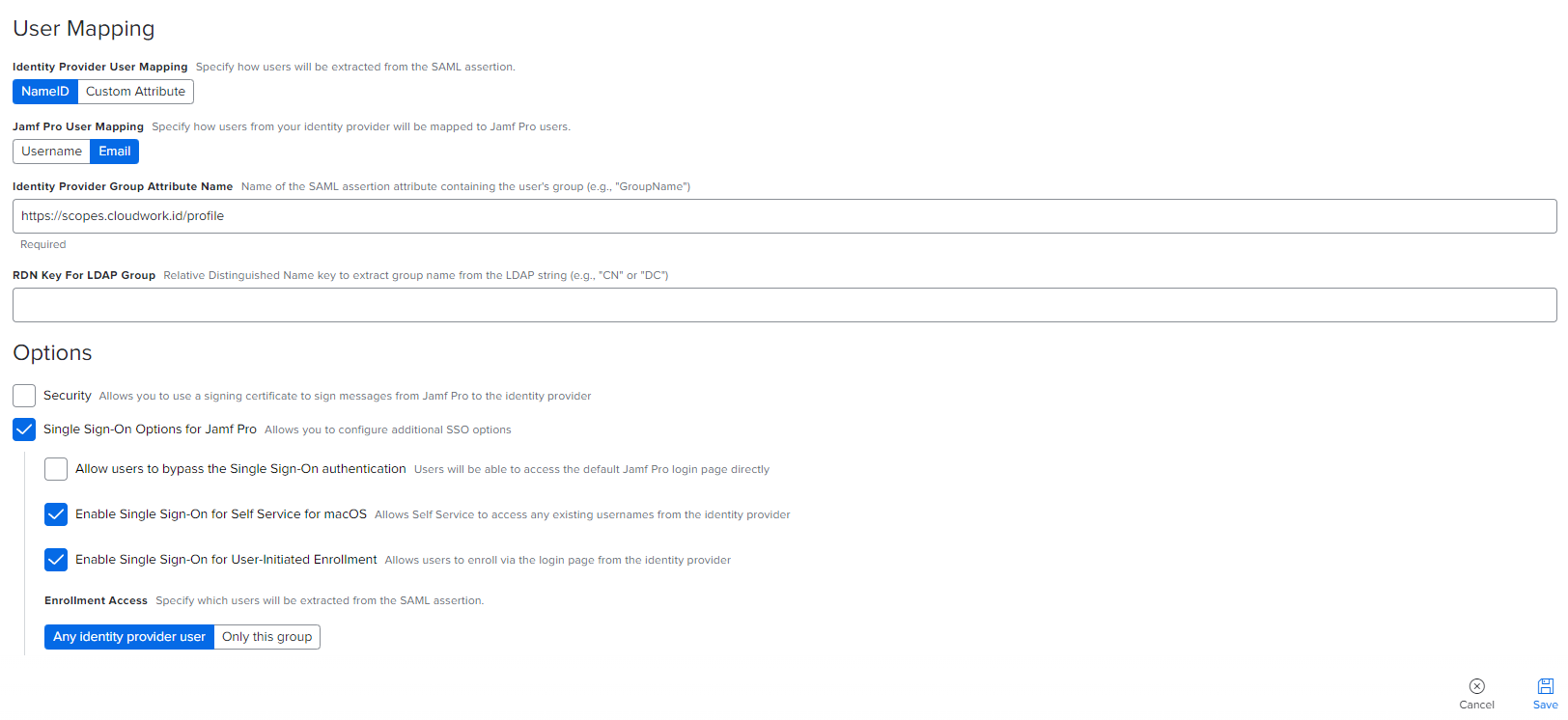
- Identity Provider User Mapping = Set to NameID
- Jamf Pro User Mapping = Set to Email
- Identity Provider Group Attribute Name = Set to https://scopes.cloudwork.id/profile
- Options: Select the following options
- Single Sign-On Options for Jamf Pro
- Allow users to bypass the Single Sign-On authentication (Optional Choice)
- Enable Single Sign-On for Self Service for macOS
- Enable Single Sign-On for User-Initiated Enrollment
- Enrollment Access = Set to Any Identity provider user
- Click Save
Testing Single Sign On
- Login to your JAMF Pro Dashboard
- In the top right corner click the gear
- Click Jamf Pro User Accounts & Groups
- Click New
- For Choose Action select Create standard Account and click Next
- Populate your test user details:
- Notes for populating test user:
- Ensure Username is full email address, and email address field is populated.
- Password entered here will be ignored
- Test SSO by opening a private browsing session and log into your JAMF Pro Server:
- If using JAMF OnPremise, login to: https://<JAMF Pro domain>:8443/saml/metadata
- If using Jamfcloud hosted server, login to: https://<JAMF Pro URL>/saml/metadata
- Notes for populating test user: