Difference between revisions of "Jamf Connect"
| (15 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | == | + | ==Jamf Connect== |
| − | + | Jamf Connect is used to allow users when logging into a Mac device to be prompted with Cloudwork's Identity Provider login, instead of the usual Mac login screen.<br> | |
| + | This is so you can create a better user experience by giving users a familiar login screen every time the user signs into a SSO Service. | ||
| − | As a part of | + | As a part of Cloudwork's support for Jamf Connect: When setting up an OAuth App in the Cloudwork Dashboard, under Allowed Grant Types, Password can now be selected.<br> |
| − | + | Password must be selected as an Allowed Grant Type when setting up Jamf Connect, this is to allow both the username and password to authenticate and authorise the user.<br> | |
| − | Password must be selected as an Allowed Grant Type when setting up | ||
| − | ===Setting up | + | ===Setting up with Cloudwork=== |
| − | |||
#Login to the '''Cloudwork Dashboard'''>'''Single Sign On'''>'''Manage OpenID Connect Apps'''>'''Add New Service''' | #Login to the '''Cloudwork Dashboard'''>'''Single Sign On'''>'''Manage OpenID Connect Apps'''>'''Add New Service''' | ||
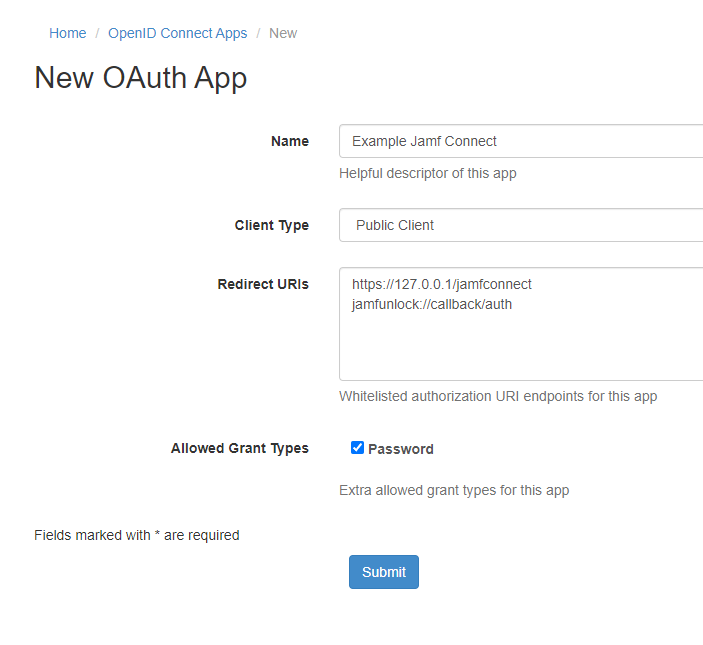
| − | #In '''Name''' enter ''' | + | #In '''Name''' enter '''Jamf Connect''' |
#In '''Client Type''' select '''Public Client''' | #In '''Client Type''' select '''Public Client''' | ||
| − | #In '''Redirect URIs''' enter the '''Redirect URIs''' | + | #In '''Redirect URIs''' enter the '''Redirect URIs''': |
| − | #For '''Allowed Grant Types''' enable the checkbox '''Password''' | + | #*'''https://127.0.0.1/jamfconnect''' for MacOS |
| − | #Click '''Submit''', you will then be redirected and see the service information. | + | #*'''jamfunlock://callback/auth''' for IOS to allow biometric authentication |
| − | # | + | #For '''Allowed Grant Types''' enable the checkbox '''Password'''<br>[[File:Example_JAMF_Connect.PNG|150px|centre|frame|Example of Cloudwork Setup]] |
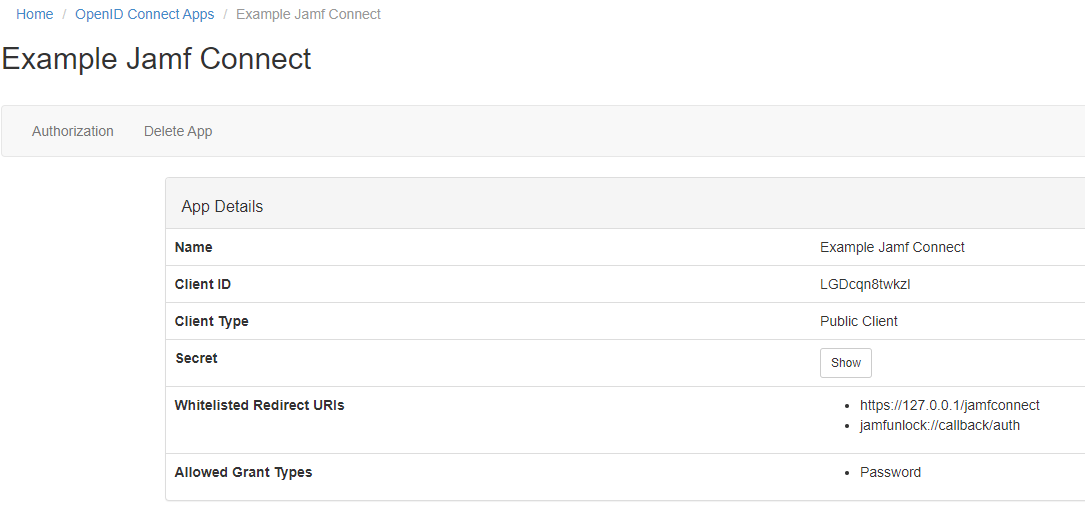
| − | + | #Click '''Submit''', you will then be redirected and see the service information.<br>[[File:Example_JAMF_Connect_App_Details.PNG|150px|centre|frame|Example of Service Information after setting up Jamf Connect]] | |
| − | # | + | #Make a note of the '''Client ID''', '''Secret'''(press '''show''' to reveal '''Secret''') and '''Whitelisted Redirect URIs''' |
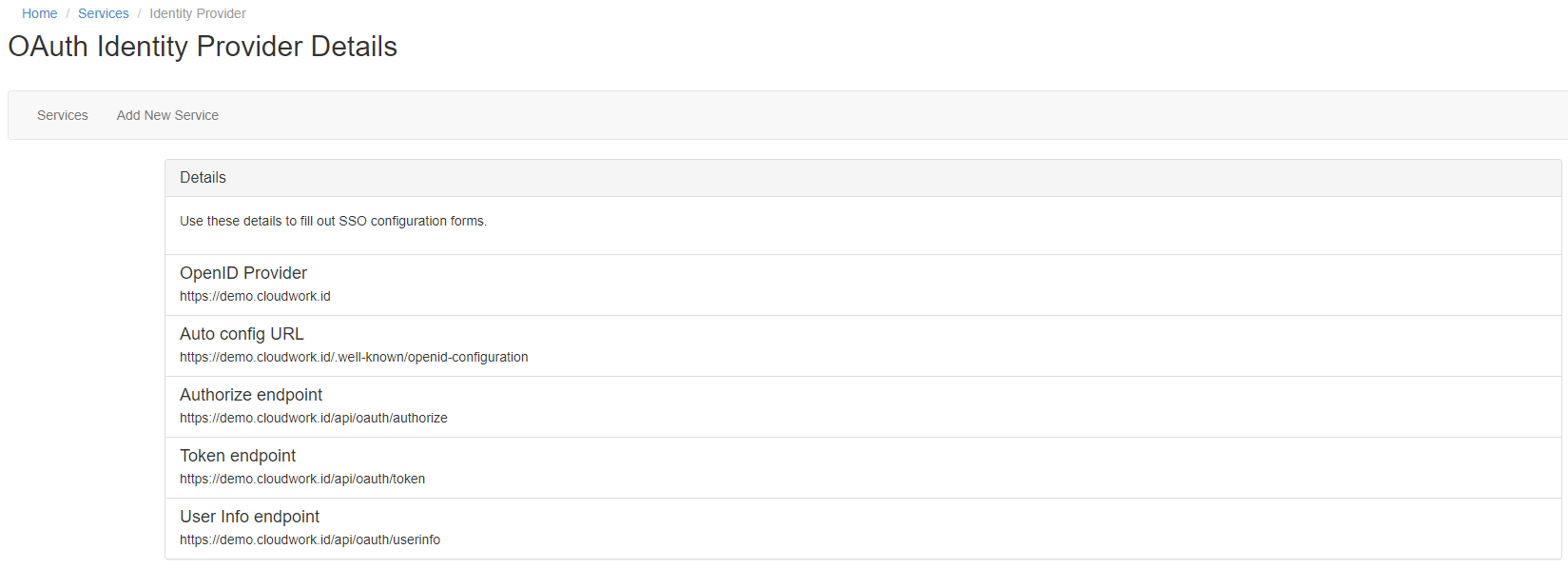
| + | #Navigate to '''Cloudwork Dashboard'''>'''Single Sign On'''>'''Manage OpenID Connect Apps'''>'''Identity Provider''' and make note of the '''Auto config URL'''<br>[[File:Oauth_idp_details.PNG|150px|centre|frame|Example of OAuth IdP Details]] | ||
| + | #Email Jamf Connect letting them know you have completed the setup on Cloudwork's end | ||
===Email Template=== | ===Email Template=== | ||
<blockquote> | <blockquote> | ||
| − | Hi | + | Hi Jamf Connect, |
Our school <schoolname> is wanting to setup a connection between Cloudwork and JAMF Connect.<br> | Our school <schoolname> is wanting to setup a connection between Cloudwork and JAMF Connect.<br> | ||
| − | + | We have completed the setup on Cloudwork's end<br> | |
Could you also provide what information you will require from us to complete the process at your end?<br> | Could you also provide what information you will require from us to complete the process at your end?<br> | ||
</blockquote> | </blockquote> | ||
| − | [[Category: | + | ==Setup with Jamf Connect== |
| + | #Login to Jamf Connect | ||
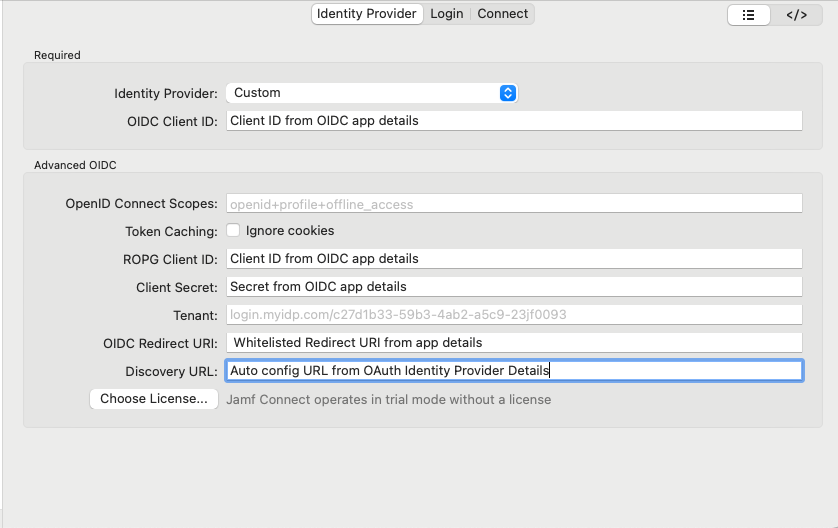
| + | #Fill out the Form as follows: | ||
| + | #*'''Identity Provider''': Select '''Custom''' | ||
| + | #*'''OIDC Client ID''': Enter the previously noted '''Client ID''' | ||
| + | #*'''ROPG Client ID''': Enter the previously noted '''Client ID''' | ||
| + | #*'''Client Secret''': Enter the previously noted '''Secret''' | ||
| + | #*'''OIDC Redirect URI''': Enter the previously noted '''Whitelisted Redirect URIs''' | ||
| + | #*'''Discovery URL''': Enter the previously noted '''Auto config URL''' | ||
| + | |||
| + | [[File:JAMF_Connect_IDP_Form.png|150px|centre|frame|Example of Jamf Connect Setup]] | ||
| + | |||
| + | |||
| + | ==Final Result== | ||
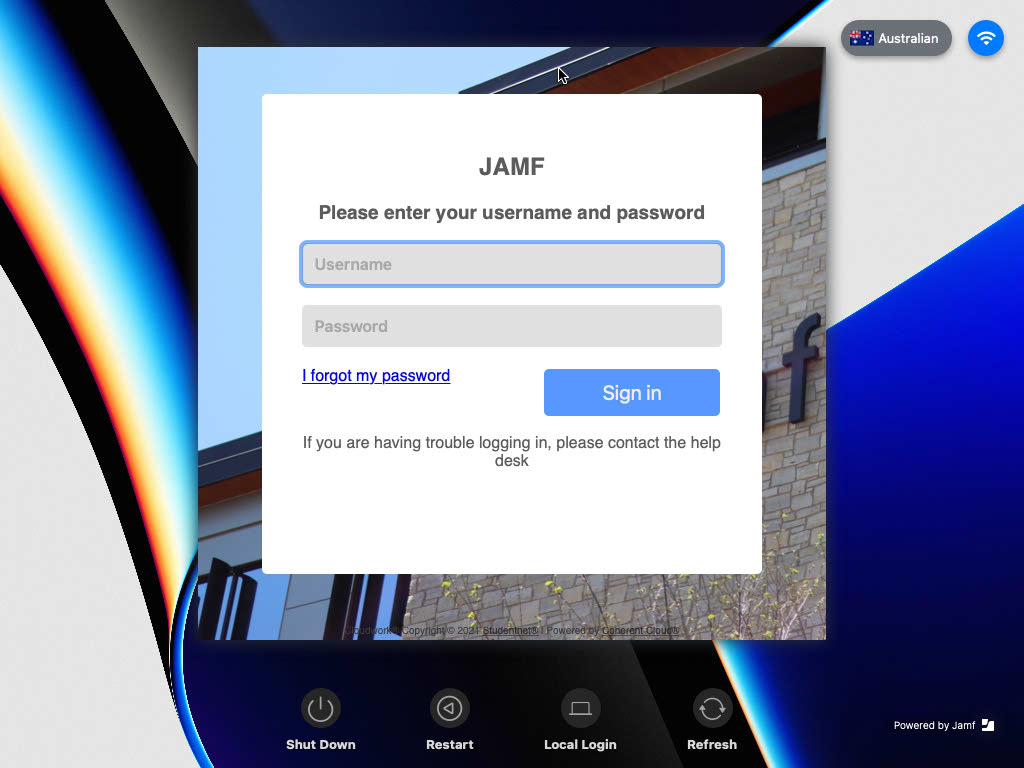
| + | Once you have completed the process on both sides, when logging into your device you should see your school's login screen. | ||
| + | [[File:Jamf_Connect_Network_Login.png|150px|centre|frame|Example of Jamf Connect when setup has been completed]] | ||
| + | |||
| + | [[Category: Single Sign On Services]] | ||
Latest revision as of 03:09, 29 August 2022
Contents
Jamf Connect
Jamf Connect is used to allow users when logging into a Mac device to be prompted with Cloudwork's Identity Provider login, instead of the usual Mac login screen.
This is so you can create a better user experience by giving users a familiar login screen every time the user signs into a SSO Service.
As a part of Cloudwork's support for Jamf Connect: When setting up an OAuth App in the Cloudwork Dashboard, under Allowed Grant Types, Password can now be selected.
Password must be selected as an Allowed Grant Type when setting up Jamf Connect, this is to allow both the username and password to authenticate and authorise the user.
Setting up with Cloudwork
- Login to the Cloudwork Dashboard>Single Sign On>Manage OpenID Connect Apps>Add New Service
- In Name enter Jamf Connect
- In Client Type select Public Client
- In Redirect URIs enter the Redirect URIs:
- https://127.0.0.1/jamfconnect for MacOS
- jamfunlock://callback/auth for IOS to allow biometric authentication
- For Allowed Grant Types enable the checkbox Password
- Click Submit, you will then be redirected and see the service information.
- Make a note of the Client ID, Secret(press show to reveal Secret) and Whitelisted Redirect URIs
- Navigate to Cloudwork Dashboard>Single Sign On>Manage OpenID Connect Apps>Identity Provider and make note of the Auto config URL
- Email Jamf Connect letting them know you have completed the setup on Cloudwork's end
Email Template
Hi Jamf Connect,
Our school <schoolname> is wanting to setup a connection between Cloudwork and JAMF Connect.
We have completed the setup on Cloudwork's end
Could you also provide what information you will require from us to complete the process at your end?
Setup with Jamf Connect
- Login to Jamf Connect
- Fill out the Form as follows:
- Identity Provider: Select Custom
- OIDC Client ID: Enter the previously noted Client ID
- ROPG Client ID: Enter the previously noted Client ID
- Client Secret: Enter the previously noted Secret
- OIDC Redirect URI: Enter the previously noted Whitelisted Redirect URIs
- Discovery URL: Enter the previously noted Auto config URL
Final Result
Once you have completed the process on both sides, when logging into your device you should see your school's login screen.